Security isn't a tool.
It's a choice.
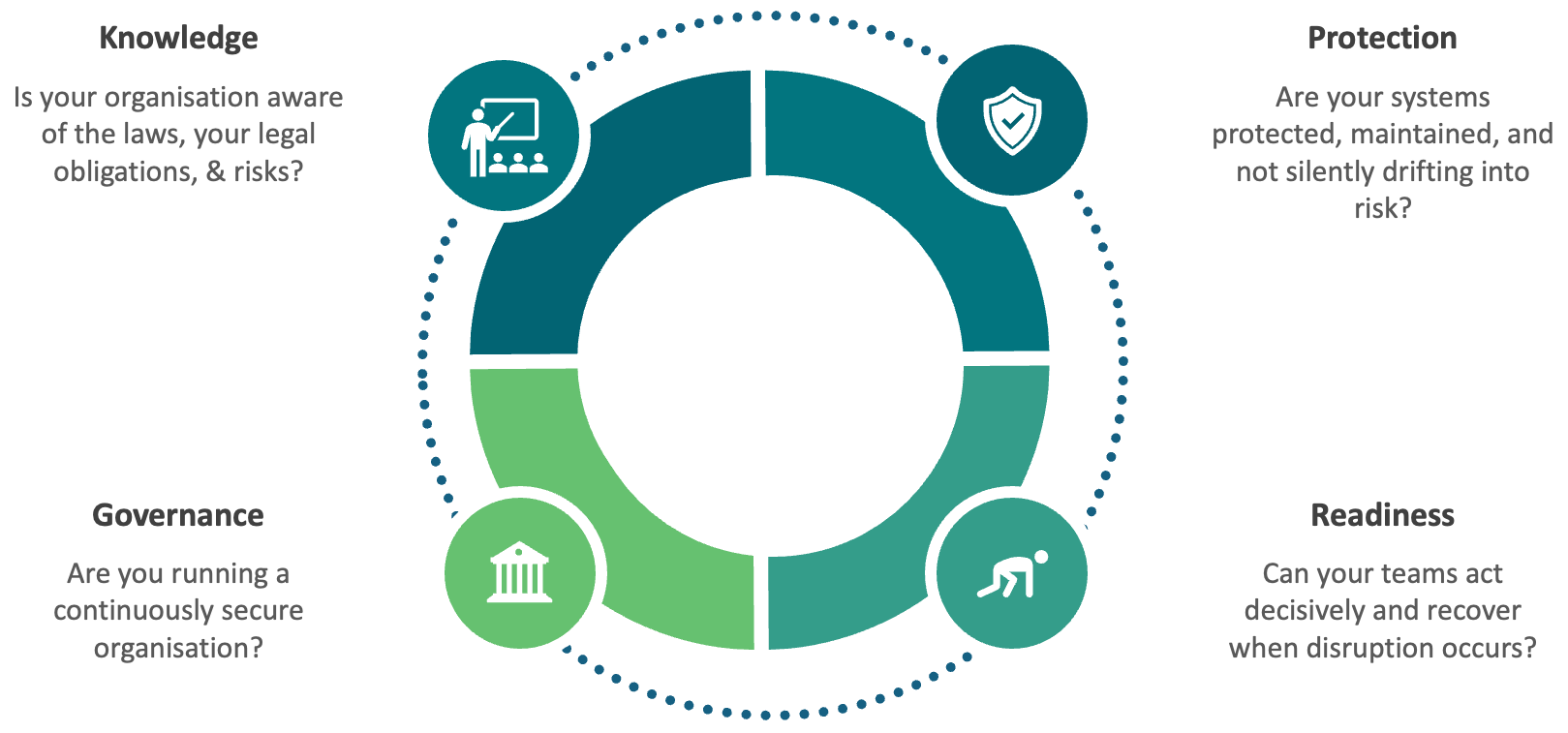
Knowledge. Protection. Readiness. Governance.
Most organisations manage training, devices, incident response, and governance in separate silos. When something goes wrong — or when a regulator asks — the gaps between those silos become visible. CONTINUITY closes them.
Silos create
blind spots.
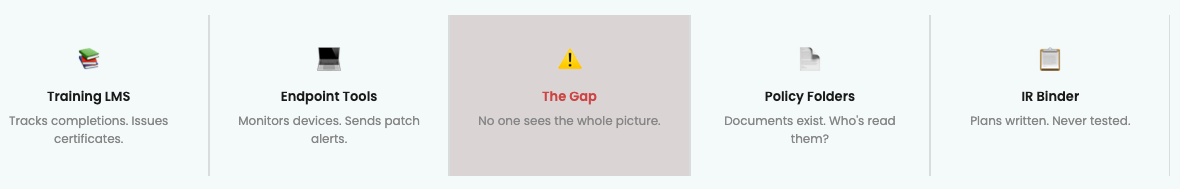
Most organisations have the right pieces. Training happens somewhere. Devices are managed elsewhere. Policies exist in a folder. Incident plans are written down. But they don't talk to each other.
That means you can have 100% training completion and still have missing knowledge. You have devices securely configured, but you're not sure if they all are. You can have a documented incident response plan that nobody has ever tested. You can have policies that live in SharePoint but were never acknowledged by the people they apply to.
Continuity isn't about having all the pieces. It's about having them connected — and visible.
Training that
changes behaviour.
Assures: Your people know what to do — and can demonstrate it.
Conversational, chat-based lessons that build real decision-making capability — not just awareness. AI-built content. No training expertise needed.
- Scenario-based chat lessons — not videos
- AI lesson builder for any topic
- Role-based learning tracks and certification
- Org-wide competency analytics
See every device.
Miss nothing.
Assures: Your systems are protected, maintained, and not silently drifting into risk.
Continuous device inventory, patch compliance, and hardware lifecycle tracking — built on CIS Level 1 baseline. Structured evidence for auditors.
- Real-time asset discovery and tracking
- Patch and anti-malware compliance monitoring
- Hardware lifecycle and decommission alerts
- Monthly evidence-ready reports
Tested plans.
Not just written ones.
Assures: Your teams can act decisively when disruption occurs.
Phishing simulations, tabletop exercises, and vulnerability assessments that turn incident response from a document into a demonstrated, measurable capability.
- Controlled phishing campaigns by department
- Scenario-based tabletop exercises
- Infrastructure vulnerability assessments
- Readiness reporting for boards and insurers
Governance that
lives in reality.
Assures: You run a continuously secure and compliant organisation — and can prove it.
Real-time posture score across Education, Protection, and Readiness. Policy management, access reviews, automated reminders, and instant audit evidence.
- Organisation-wide cybersecurity posture score
- Policy assignment, tracking, and acknowledgment
- Automated review cycles and deadline alerts
- One-stop reporting for CEM, CTM, DPTM, HIA
Assurance Should Be Continuous.
Not Reactive.
Each product in the CONTINUITY suite works independently. But the real value emerges when they're connected — when training data feeds your governance posture score, when device compliance informs your risk picture, when phishing simulation results trigger targeted learning.
No point solution gives you that. CONTINUITY is the only platform that makes your entire assurance posture visible, connected, and continuously improving.

StaySecure CONTINUITY™ is continuous assurance.
Built for organisations that
take security seriously